TYPES OF CYBER ATTACKS IN DETAIL...!
Cyber attacks are becoming increasingly common, and it's important for individuals and businesses alike to understand the different types of attacks that exist. Here's a detailed overview of the most common types of cyber attacks:
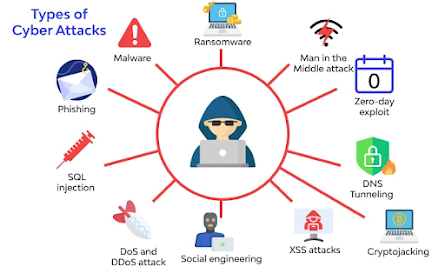
Phishing: Phishing attacks are designed to trick individuals into revealing sensitive information, such as passwords or financial details. These attacks can take many forms, such as emails, text messages, or phone calls, and are often disguised as legitimate requests from trusted organizations.
Ransomware: Ransomware is a type of malware that encrypts a victim's data and demands payment in exchange for the decryption key. These attacks can cause significant disruptions and can be extremely costly, as victims may be forced to pay the ransom in order to regain access to their data.
Distributed Denial of Service (DDoS): DDoS attacks are designed to overload a website or network with traffic, making it unavailable to users. These attacks can be initiated from a large number of sources and can cause significant damage to a business's reputation and finances.
SQL Injection: SQL injection attacks are a type of code injection that target databases. The attacker injects malicious code into an SQL database, allowing them to extract or manipulate data. These attacks can be particularly devastating, as they can expose sensitive information and compromise the security of an entire organization.
Malware: Malware is any type of software that is designed to cause harm to a device, network, or data. Malware can take many forms, including viruses, Trojans, and spyware, and can cause significant damage if not properly detected and addressed.
Man-in-the-Middle: Man-in-the-middle attacks are a type of interception attack in which the attacker intercepts communication between two parties and steals data or alters its content. These attacks can be particularly difficult to detect and can have devastating consequences.
Cross-Site Scripting (XSS): Cross-site scripting (XSS) attacks are a type of code injection that target websites. The attacker injects malicious code into a website, compromising its users. These attacks can lead to the theft of sensitive information, such as login credentials, or the exploitation of vulnerabilities in the targeted website.
Zero-Day Exploits: Zero-day exploits are attacks that take advantage of vulnerabilities that are unknown to the targeted software's creators. These attacks can be particularly devastating, as they can occur before a patch or fix has been made available.
Password Attacks: Password attacks are attempts to gain unauthorized access by cracking or guessing passwords. These attacks can be initiated through a variety of methods, including brute-force attacks, dictionary attacks, and social engineering tactics.
Internet of Things (IoT) Attacks: IoT attacks are a type of cyber attack that target smart devices connected to the Internet. These devices can be vulnerable to exploitation, as they often lack proper security measures and can provide an entry point into a larger network.
It's important to be aware of these types of cyber attacks and to take steps to protect yourself and your organization from potential threats. This can include regular software updates, strong passwords, and the use of security solutions such as firewalls and antivirus software.


Comments
Post a Comment